Edited by: Abbas Mardari
More infoThis work aims to expand the understanding on the nature of institutional innovation and the goal of knowledge innovation of intellectual property (IP) law in the era of big data (BD) and to avoid the risks of information security in the IP service system. On the basis of the era of BD, the nature of institutional innovation and the goal of knowledge innovation in IP law are systematically discussed. Combined with smart contract (SC) technology, an IP service system based on blockchain technology is designed to ensure the security of IP services. The SC is optimized from the perspective of concurrency, and the contract transactions (CTs) are clustered. Moreover, considering the execution time (ET) and available resources of CTs, a speculative concurrency control algorithm that can realize intelligent contract scheduling is proposed. On the basis of the ciphertext-policy attribute-based encryption (CP-ABE) algorithm, a policy-updatable attribute encryption algorithm is designed. The improved CP-ABE algorithm includes six steps: system initialization, attribute private key generation, encryption, decryption, ciphertext policy generation, and ciphertext policy update. The identity parameter of the traceability manager is introduced into the improved CP-ABE scheme, which significantly increases the amount of computation of bilinear mapping, thus resulting in the time cost of encryption and decryption being approximately 350 ms and 300 ms higher than that of the CP-ABE scheme. Using the technical mode of “blockchain + SC,” the design of the IP service system is realized, which has important reference value for the institutional innovation of IP law.
With the gradual availability and popularization of unlimited communication, data have developed from small scale to large scale, and information is growing. The data sources of big data (BD) vary, including meteorological information collected by sensors from all over the world, data on social media websites, financial and transaction records, etc. In the business environment, BD means that an organization must access a large amount of unimaginable structured and unstructured data (Hussien, 2020; Zohuri & Moghaddam, 2018; Alazie & Ebabye, 2019). Enterprises must realize that by capturing, constructing, and analyzing these massive data, they will obtain valuable insights, thereby improving their business methods. In addition, organizations must use data analysis tools to capture, process, store, search, analyze, and share these valuable data. The largest value of BD is to mine valuable data for future trend and pattern prediction and analysis from a large number of irrelevant data of various types. Through an in-depth analysis of machine learning, artificial intelligence (AI), and data mining methods, new laws and new knowledge have been found and applied to various fields, such as agriculture, finance, and medical treatment, thus finally improving social governance, enhancing production efficiency, and promoting scientific research (Lv et al., 2020).
With the increasing popularity of BD technology in all aspects of social life, judicial innovation will also become an important test field for the implementation of the BD technology industry. The legal framework of BD is divided into two levels: the first level is physical infrastructure, as well as software; the second level is information architecture (Williamson & Ben, 2018; Gong & Janssen, 2020). BD faces numerous challenges in privacy. In addition to cloud computing and other computing frameworks, large storage capacity and efficient data processors are the key factors affecting BD privacy. The current era of data involves the superposition of the Internet, BD, and AI. As such, the full protection of personal information is facing challenges. Most of society lives in a transparent environment without privacy. However, user data are a valuable social resource in the era of BD. This resource is also an important guarantee for industrial subjects to produce and open information. Hence, it has high property value and needs to be discussed in combination with the protection of intellectual property (IP) (Chen et al., 2020; Pang, 2021; Georgiadis & Poels, 2021).
At present, European countries are exploring the protection of database authors with independent rights, and countries worldwide also attach great importance to the protection of data property (El-Taliawi et al., 2021). Different from the data storage and data transmission in the Internet era, the BD era focuses on the deep mining of data and the wide application of data, which brings new opportunities for IP protection. In the BD era, the protection of enterprise IP is no longer as simple as the protection of IP. It also covers services in various fields, such as information security, enterprise legal affairs, and government relations (Hui & Wei, 2021; Machowicz, 2021). Given that the acquisition of resources is more transparent under BD, traditional “patent only” or “problem oriented” thinking has not met the needs of enterprises. IP protection is only the starting point of enterprise innovation and development in the era of BD (Vimalnath et al., 2022). Whether enterprises can effectively carry out enterprise innovation protection and business competition through comprehensive solutions is the key to whether enterprises can realize value in the new era (Liu & Shestak, 2021).
Relying on its own scientific research platform, the university adheres to the high-quality construction of IP projects, constantly cultivates the IP awareness of students and teaching staff, gradually improves the IP management system, and steadily conducts the education and management of IP protection and application of specific work. It has achieved remarkable results in promoting the cultivation of innovative talent and the output of innovative achievements. Independent innovation is inseparable from IP protection, and IP needs to be protected by relevant legal systems. As such, this work aims to analyze the nature of institutional innovation and the goal of knowledge innovation in IP law in light of the characteristics of the era of BD. Given that IP law is born and exists on the basis of the needs of institutional innovation, this work further discusses the value of IP law and the obstacles to its realization, which lays a good foundation for the enhanced exploration of IP protection methods in the future. This paper is structured as follows. Section 2 summarizes the existing research on enterprise IP protection. Next, Section 3 explains the innovation mode of IP protection and designs the IP protection scheme on the basis of blockchain technology. In Section 4, an experiment is designed to evaluate the performance of the BD IP service system and analyze the data traceability performance of the IP service system. Finally, the whole work is summarized, and the research value is explained.
Related workIP protection in the era of BDBD is defined by four factors, namely, capacity, diversity, speed, and accuracy, which provide a new way to analyze and manage unstructured data. BD is not only the collection of massive data but also the collection, storage, and correlation analysis of data collection. BD has the characteristics of typical intangible properties. The formation of BD requires considerable labor, and the results are of high value. Moreover, BD is a typical IP and should be protected according to law (Müller, Fay, & Vom, 2018; Appelbaum, 2016). It is different from the characteristics of patents, trademarks, copyrights, and other IP rights. Hence, the means to protect BD remains a controversial issue in academic circles. The collection of obtained data, data processing of machine analysis, and analysis results expressed in the form of reports constitute the different stages of the formation of BD. Given the different means, the right characteristics of its IP are also different, which cannot be generalized by copyright.
Andanda (2019) believed that BD analysis should promote the reform of adjudication methods in line with the law of IP litigation, explore and determine the amount of infringement damages that truly reflect the value of IP, improve judicial efficiency, and optimize the effect of dispute resolution. In the new network scene, IP infringement and unfair competition are intertwined, which shows its complexity. Algorithm recommendation is the behavior in which network service providers use an algorithm mechanism to push information to users. At present, whether in the field of short video, live broadcast, or e-commerce, algorithm recommendation generally exists in the Internet ecology. The current information flow can be regarded as an algorithm recommendation. Of course, various forms of logic have been recommended, such as collaborative filtering and personalized recommendations. Algorithm recommendation has attracted much attention in IP infringement cases, which is related to the safe haven rule. Schwartz (2019) pointed out that the applicable condition of the safe haven rule entails that network service providers are in a neutral position in the face of a large amount of content generated by third parties. If they are not neutral, they cannot enter the safe haven. In this sense, if the network service provider substantially contacts the content by recommending, modifying, and editing, it violates neutrality. With the rise of IP service platforms and institutions, how to use BD technology to enhance work efficiency, improve customer satisfaction, control costs, and even change the future industry pattern will be an unavoidable problem for the IP industry.
Knowledge innovation in IP lawThe main driving force of social progress is scientific progress in which IP is an important component. Therefore, protecting IP has become an important task. The protection of IP has stimulated people's enthusiasm for invention and creation and promoted social and economic development. Zakieva et al. (2019) presented that the legal essence of the survival and development of IP law lies in institutional innovation. Innovation is the key to the future. The integration of IP and BD will create a new industrial ecosystem. BD provides direction and a foothold for the application of IP, while IP escapes innovation and development. Furthermore, BD connects fragmented and independent IP “information islands” and “application islands,” thus obtaining a new IP business form of information sharing. Brescian et al. (2021) pointed out that IP protection can be used in the whole process of BD analysis and all fields of innovation and development, which should not only prevent data resource monopolies and protect innovation power but also encourage the sharing of data-based resources to maximize efficiency.
Institutional innovation usually refers to the activities of institutional subjects to obtain additional benefits through new institutional construction (Brous et al., 2020; Qi & Chau, 2018). For IP law, it provides a new way for people to obtain property at the institutional level. Its institutional innovation is essentially the reform of the existing system and the deployment of the new system. IP law has independent dominant value, that is, innovative value. All IP laws are the product of their social, economic, and political environment. They define the property rights of innovation activities and provide corresponding incentive mechanisms. The development and continuous improvement of IP law is the result of the promotion of modern scientific and technological powers and economic powers. At the international level, it should take the establishment of a fair and reasonable international order of IP as the fundamental principle and then actively promote the reform of the international IP system.
BD and privacy challengesWith the BD processing of large data sets, making the connection faster and more reliable will greatly improve their function. Pang (2021) indicated that personal data sharing has several problems, such as privacy and convenience. The use and circulation of future data should be based on protecting personal privacy and data security. Moreover, the abuse and illegal resale of various data will lead to issues in the development of the industry. In the era of data security 1.0, data can only enter through means that include network security, structural security, and system security to turn the data system into a secure sandbox and become unbreakable. This method not only protects the data but also hinders the circulation of data value, thus preventing the data from fully playing their value function. This constraint is not desirable in the current era, which emphasizes that data should become a factor of production. Fiske et al. (2019) concluded that privacy computing technology based on cryptography and trusted hardware environments can realize the circulation of data value on the premise of ensuring data security. It is an important infrastructure for data to become a factor of production. This advancement is called the era of data security 2.0, which makes data open in security and secure when open. At present, privacy computing technology is still in the early stage of development, and the maturity of technology and products has much room for improvement.
Research reviewFrom the current academic research on IP and technological innovation, the studies that comprehensively consider and investigate property rights and technological innovation are scant. Hence, on the basis of the era background of BD, the essence of institutional innovation and the goal of knowledge innovation of IP law will be systematically discussed. In addition, considering that the management of IP works mainly depends on the centralized authoritative management organization, certain risks in information security emerge. Therefore, smart contract (SC) technology will be combined to design an IP service system based on blockchain technology to ensure the security of IP services.
Knowledge innovation and security protection in IP lawBD technology-driven IP protectionThe huge value and broad development prospects of IP BD have attracted many enterprises to engage in the R&D and application of IP BD. The important feature of BD technology is its ability to collect and analyze all data, as IP analysis requires checking the whole data. Therefore, BD can play a highly comprehensive application value in the layout of IP. At this stage, numerous institutions engaged in IP services attach great importance to the accumulation, construction, and application of BD resources. In addition, they have attempted to explore new data application modes and have achieved certain results. However, the mining of IP BD is still in its infancy. In the retrieval process of trademarks, patents, and copyrights, the total amount of IP applications and the massive data resources generated in the application process provide a huge data foundation for the application of BD in IP retrieval (Kwon, Lim, & Lee, 2021; Tella, 2021). Moreover, with the rapid growth of basic applications for IP, retrieving the similarity of IP through traditional manual methods has become increasingly difficult and intensive. BD AI can carry out effective data cleaning and data comparison for such mechanical work and gradually complete the functions of machine learning and improvement.
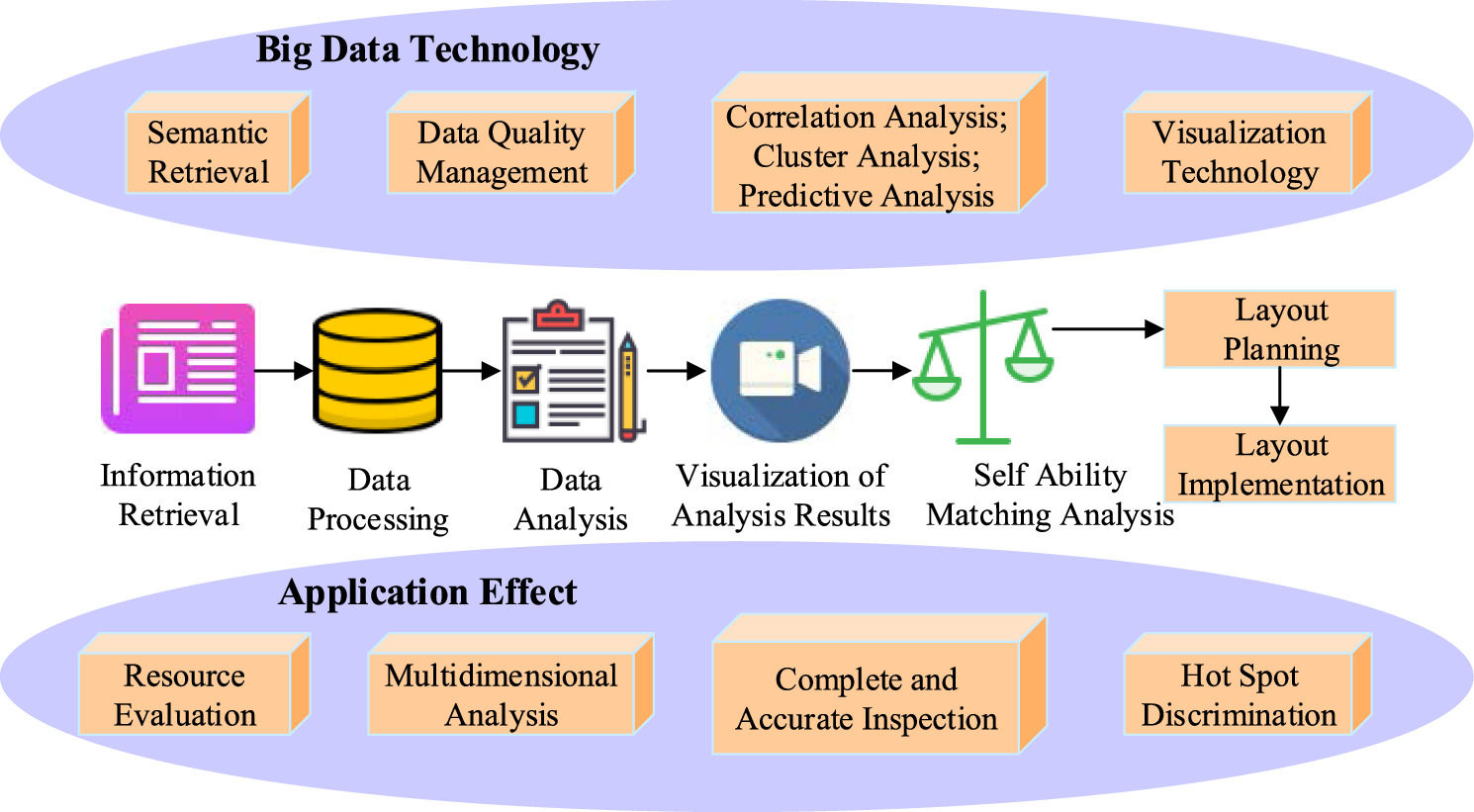
Fig. 1 shows the IP layout model supported by BD technology. In the layout of IP, BD technologies mainly include semantic analysis, correlation analysis, predictive analysis, and visualization technology. First, given the natural language characteristics of patent documents, they contain a large number of similar general descriptions and rhetoric. Therefore, the context is complex. Semantic analysis based on BD technology can not only efficiently complete semantic retrieval but also realize higher-level intelligent retrieval, such as graphic and chemical equation retrieval (Maniou, 2021). Mining data from IP information and analyzing its correlation can make the layout of IP more reasonable. The Hadoop Distributed File System (HDFS) can provide high-throughput data in the form of a stream when accessed and provide support for mining the relevance of data information (Rajeh, 2022). Predictive analysis can help enterprises complete the forward-looking layout of IP strategy. Finally, the information in BD is extracted in the form of generalization, and the multidimensional analysis results are intuitively displayed in the form of charts, which is conducive to promoting the application of the IP layout. Such data visualization technologies include Echarts, QlikView, FineBI, etc. The implementation of the IP layout is highly important and requires the cooperation of all staff. The R&D department is the key to layout implementation, which directly determines whether the expected objectives in layout planning can be achieved.
Patent data have inherent advantages over other data (Li et al., 2021). If a complete industrial technology context and market distribution are established on the basis of patent BD analysis, it will provide a reliable benchmark for the establishment of evaluation algorithms with full consideration of legal, technical, and economic factors (Fredstrm et al., 2021; Kang et al., 2021). Compared with the existing evaluation methods, the patent value evaluation based on BD analysis will be more comprehensive and objective. From the perspective of evaluation, it can approach its real value from the legal and technological essence of the patent and can also take the industrial output value as the scientific basis to reflect the market value of relevant patent rights more specifically.
Knowledge innovation model of IP protectionThe IP law stipulates the subject and ownership of exclusive rights, the conditions and procedures for obtaining rights, and the content of rights. As long as innovation organizations cooperate in accordance with the guidance of legal norms, they can obtain the corresponding exclusive rights and the future rights and interests they represent. These clear institutional designs have the function of promising exclusive rights and stabilizing the expectations of creators. Inventions and utility models can be patented only if they have the elements of novelty, creativity, and practicability (Grimaldi et al., 2021). The key to understanding, adapting, and promoting innovation and development is to respect and apply the law of innovation and establish an innovative system view. The innovation system involves the habit and legal rule of organizing resources, coordinating the relationship between organizations, and distributing interests, among which the most important is the IP system.
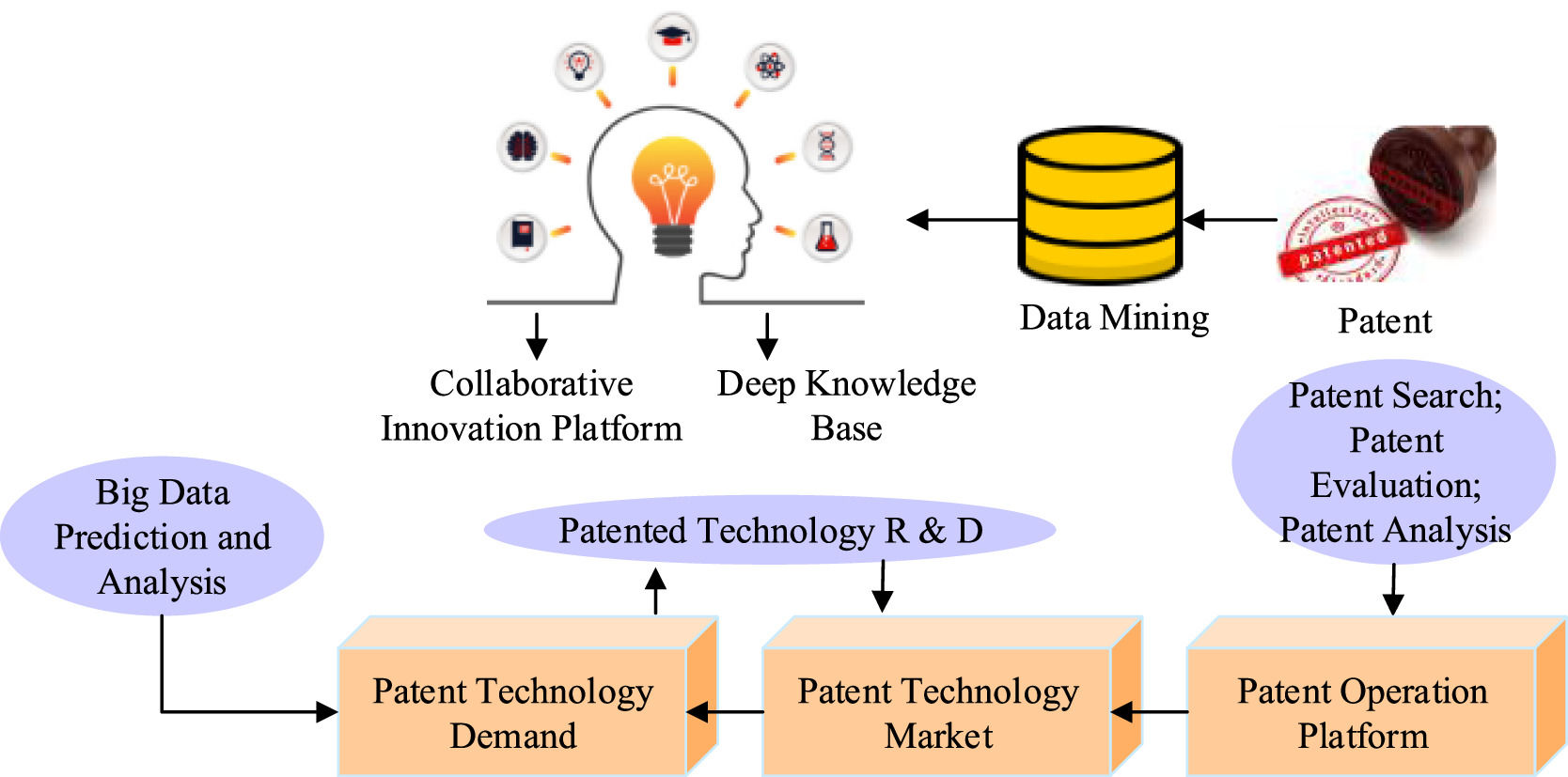
IP and BD, as an unprecedented force of national basic strategic resources, lead to the development of the economy and society (Roh Lee & Yang, 2021; Hao et al., 2021; Nebus Chai, & Subramanian, 2021). Under the background of the BD era, the innovation modes of patent operation are summarized, which mainly include the efficient R&D mode of patent technology, the comprehensive government-led mode, and the combination mode with university R&D teams. Fig. 2 shows the ecosystem based on the innovative model of patented technology development and operation. The in-depth patent knowledge base can provide a case reference, which is conducive to discovering technology, promoting the efficient operation of technology R&D, and finally operating and transforming patented technology. In the comprehensive government-led operation innovation model, patent innovation comes from colleges and universities, and enterprises belong to the source of transformative technology. The government is responsible for providing funds and policy support and promoting the sustainable R&D work of colleges and universities. In the operation innovation mode combined with the university R&D team, a tripartite profit distribution mechanism must be established among operation institutions, enterprises, and universities to promote its sustainable operation.
System and knowledge innovation network based on knowledge sharing within the clusterBased on its theoretical basis, the “global channel” bridges innovation resources in different spaces; meanwhile, interregional connections promote competition among innovation subjects, thus accelerating the flow of global knowledge, capital, and talent (Rauch & Ansari, 2022; Gupta, 2021). Fig. 3 shows the impact of global knowledge networks on organizational knowledge innovation. On the one hand, introducing global knowledge into the organization can reshape the knowledge structure of the innovation organization and affect the knowledge-sharing mode in the cluster. On the other hand, cross-regional cooperation will be accompanied by the transfer of knowledge networks. In addition, the knowledge network within the organization will also overflow and spread to the outside, which can substantially change the position of the organization in the global knowledge network. Corresponding to the global channel is “local buzz,” that is, local interaction, which will promote the establishment of local conventions and other institutional arrangements. The informal connection built by local buzz and global channels plays an important role in the internal knowledge acquisition of clusters at all spatial scales. The construction of both will appear in the process of local and national industrial strategic cooperation.
Global and local cross-level network connections have played a joint role in knowledge innovation, which will subsequently have a large impact on this innovation. A global knowledge network is an organizational system with a modular structure that enables enterprises to transfer and share their available intangible assets, especially their own knowledge. From a dynamic point of view, a knowledge network is a work system, a process of knowledge creation and sharing. Compared with its static attribute as an “organizational structure,” the dynamic attribute of the knowledge network as a “work system” is more important. Under the embedding of the global knowledge network, from the level of knowledge structure, the technical knowledge network has an evident impact on the innovation of local knowledge. Moreover, the innovation of local knowledge will be regulated by the scientific knowledge network (Siew, 2022). From the perspective of spatial scale, the global knowledge network can provide global innovative knowledge, while the local knowledge network can provide a basic guarantee for the absorption and transformation of innovative knowledge (Tengö et al., 2021; Lydon-Staley et al., 2021; Bouncken & Barwinski, 2021). On this basis, the key models of the impact of global knowledge networks on knowledge sharing in local clusters are summarized (Fig. 4). In the process of globalization, organizations interact with various subjects in the knowledge innovation network. Therefore, the knowledge innovation of organizations is directly affected by the embedding of the global knowledge network. Given the great differences in the development stages of innovation organizations, the degree to which they can absorb and transform knowledge is also different.
IP protection based on blockchain technologyIn the industrial context involving a large number of IP rights, blockchain and its related distributed ledger technology provide obvious possibilities for IP protection and registration; moreover, they can be used as evidence at the registration stage or in court (Song et al., 2021). Blockchain also promises to accelerate these processes in a cost-effective manner. Potential use cases include evidence of creator and source authentication, registration, and settlement of IP; control and tracking of the distribution of (unregistered) registered IP; digital rights management; establishment and enforcement of IP agreements, licenses, or exclusive distribution networks through SCs; and real-time remittance to the IP owner.
IP service management mainly includes the business management of copyrights and patents. It can encode IP “smart information” in protected content, such as songs or images in digital form (Rejeb et al., 2021; Hauck, 2021; Wang et al., 2021). When comprehensively designing the overall architecture of the system, the characteristics of the IP service field are first considered. Then, it is closely combined with blockchain technology, after which the new mode of integration of the two is realized. The final IP service system is divided into five layers from bottom to top (Fig. 5), namely, infrastructure, data resource, storage, service, and presentation layers. The main function of the infrastructure layer is to ensure the normal development and operation of the whole system. The data resource layer includes original works produced by various intellectual creations. The storage layer mainly realizes the storage of key information using blockchain technology. The service layer is mainly responsible for providing services related to patent and copyright business management. The presentation layer is mainly for different users, and users can also change IP works.
The SCs are optimized, and contract transactions (CTs) are clustered from the perspective of concurrency. Moreover, a speculative concurrency control algorithm that can realize intelligent contract scheduling is proposed. First, the FIA unit is set to make real-time statistics on the conflicting contract characteristic information in the process of CT scheduling and management, and the collected characteristic information is taken as the key factor to solve the contract conflict. The interaction mode of SC includes internal calls and external calls. Therefore, the statistical analysis of characteristic information by the FIA-Unit can be divided into two types: conflicting contract account sets (C-CA sets) and high conflict rate member function sets (H-CRMF sets).
The performance of the concurrent execution of blockchain will be greatly affected by the distribution of CTs. Therefore, the CAM-Unit is set, which can divide the CTs into different sets to optimize the concurrency. The CAM-Unit will limit the number of CTs and control the concurrency acceleration ratio Scon.
where Tser and Tcon refer to the time of the serial execution of CTs and concurrent execution of CTs, respectively; Wser and Wcon refer to the load of the serial and the concurrent parts, and ∂ refers to the proportion of the serial part.CTs will consume bandwidth (B), storage (S), and computing (C). Therefore, a template containing these three consumption factors is constructed, namely, {B,S,C}. CTs similar to CTs Jsc are selected. Finally, set G*〈sc,j〉 is formed. The calculation of numerical similarity between contracts Jsci and Jscj can be expressed as follows.
After obtaining a similar set G〈sc,j〉 of Jsc, the mean value method is used to calculate the mean value of the execution time (ET) of the contract in G〈sc,j〉. Then, it is taken as the prediction time of Jsc.
where Ri indicates the actual ET of the i-th contract in G〈sc,j〉.Before the SC is executed, the conflict rate (CR) in the past period needs to be calculated first to predict the current SC conflict effectively. The calculation of the original CR Cr′ is as follows.
where Cr′ means the n prediction result, and Un−i means the CR of the n−i period.To solve the limited prediction accuracy caused by the lack of effective feedback of the calculated prediction value, the weighted moving average method is adopted, and the calculation of the feedback value is as follows.
where Fn is the n feedback value, Crn−m is the n−m final prediction value, and vm is the weight value.For the calculation of Cr′ and Fn in Eqs. (6) and (7), the corresponding weight value needs to be calculated.
The final predicted value Cr can be obtained by comparison between Cr′ and Fn.
After calculation, the estimated ET Et and CR Cr of CTs can be obtained. After comprehensive consideration, the threshold can be judged. The calculation of the aggregation function is expressed as follows.
where α is a parameter, and wt and wr represent the weights of ET E and CR Cr.In the CT scheduling management module, the Speculative Concurrency Control (SCC) algorithm is improved, and the Variable Shadow Speculative Concurrency Control (VS-SCC) algorithm is presented to execute SCs concurrently. The VS-SCC algorithm comprehensively considers three factors: resource utilization R, estimated ET Et, and CR Cr. Then, it calculates the required number of images N.
where e is a constant, and ϕ is a constant coefficient. Ro refers to the average free resources of the system, Cr(Tsc) refers to the CR of CTs Tsc, and R(Tsc) indicates the available free resources of Tsc.To execute SCs concurrently, the VS-SCC algorithm needs to be used to identify conflicts in running CTs and allow the master node to record the conflict relationship between transactions in real time to form conflict records.
To realize the dynamic protection of transaction privacy, the classical attribute-based encryption (ABE) algorithm is used as the theoretical basis. The ABE algorithm does not need to pay attention to the identity of the receiver. Only users who meet the attribute requirements can decrypt the ciphertext to ensure the confidentiality of the data. On the basis of the ciphertext-policy attribute-based encryption (CP-ABE) algorithm, a policy-updatable attribute encryption algorithm is designed. In this algorithm, the user's private key is related to a series of attributes. The ciphertext can be decrypted only if the user's attributes comply with the access structure of the ciphertext. The improved CP-ABE algorithm includes six steps: system initialization, attribute private key generation, encryption, decryption, ciphertext policy generation, and ciphertext policy update.
The system initialization algorithm is adopted to input the security parameters k and system attribute set U. The system public‒private key pair (PK,MSK) can be output.
where PK and MSK represent the primary public key and primary private key of the system, respectively.G1 is a cyclic group of the q order, g is a generator of G1, and the output system key pair (PK,MSK) is as follows.
By inputting the master private key of system MSK and user attribute set S, the output of user attribute private key SK can be obtained.
The encryption algorithm can output ciphertext CT by inputting plaintext m, identity δ of the policy updater, and access control policy (M,ρ).
The final ciphertext CT is as follows.
where (Ci,Di) indicates the part with access control policy.In the decryption link, the ciphertext CT about the access policy (M,ρ) and the private key SK related to the user attribute set S are input. Then, the plaintext m is output through the decryption algorithm. According to the linear secret sharing scheme, Eq. (20) is obtained.
where s is the secret sharing key, and λ is the secret sharing share. v represents the random vector selected by the encryption algorithm. Then, the decryption equation is as follows.The final ciphertext information m can be expressed as Eq. (22).
The output of the new ciphertext policy can be obtained by using the ciphertext policy generation algorithm.
Finally, the identity signature message 〈δ〉 and ciphertext policy information {Cδ′,(Ci′,Di′)} of the updater are input. The ciphertext policy update algorithm is used to update the access policy, and the updated ciphertext CT′={C,Cδ,(Ci′,Di′)} is output after verification.
Experimental analysisJava language is used to simulate the real intelligent contract execution. Moreover, the random class is used to achieve the uniform distribution of transaction types. The proposed concurrency execution policy is compared with the SCC algorithm before optimization and two traditional concurrency control strategies (LOCK and BTO algorithms). The average acceleration of each method is simulated.
To verify the effectiveness of the traceability scheme of the copyright protection service system based on blockchain, the C++ language is applied to simulate the attribute encryption scheme based on the CP-ABE algorithm and the attribute encryption scheme based on the improved CP-ABE algorithm. The time performance of the two schemes is compared.
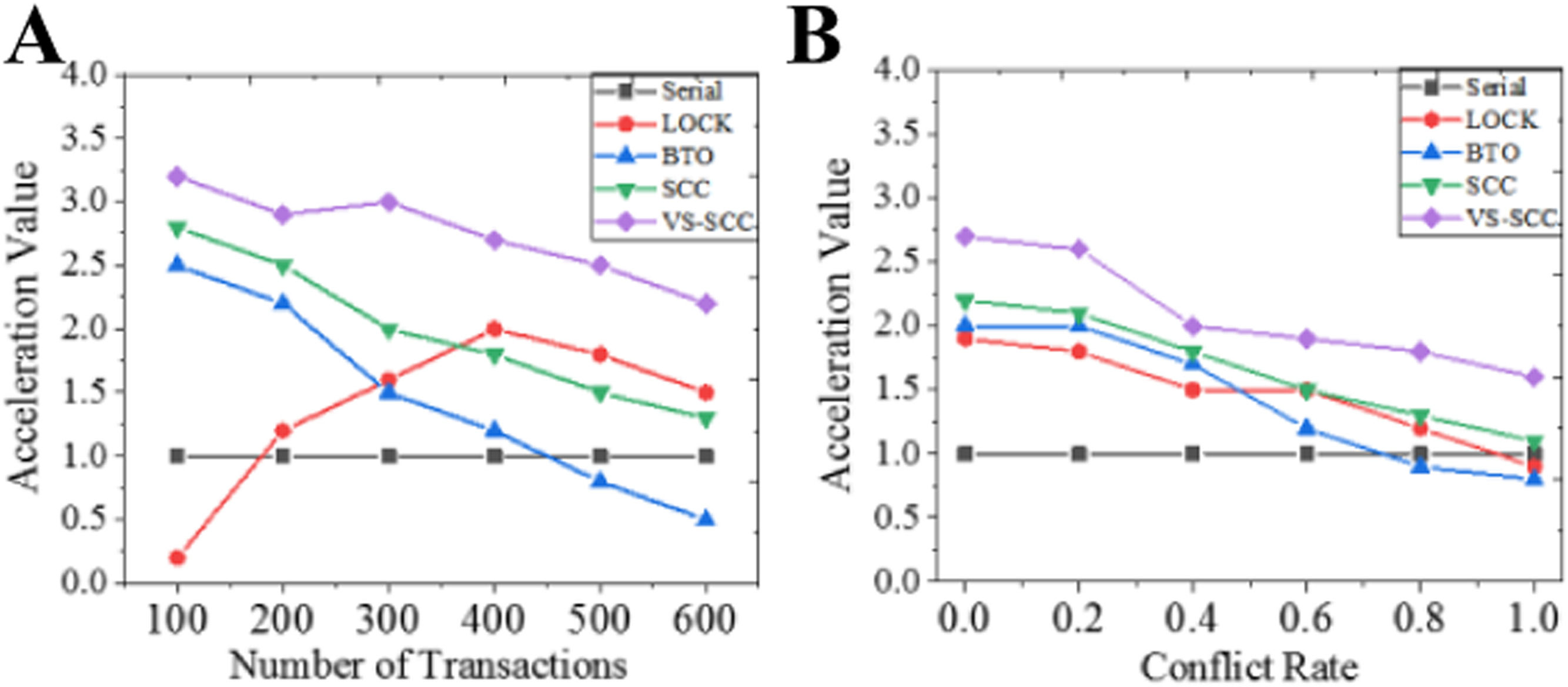
Performance evaluation of BD IP services systemConcurrent execution performance analysis of the IP service systemFig. 6 shows the acceleration changes of different concurrency control strategies when the number of transactions and CR change. When the number of transactions is low, acceleration does not occur due to the additional overhead caused by the conflict processing of the LOCK algorithm, which has a direct impact on the concurrency performance of the system. With the continuous increase in the number of transactions, the acceleration value of the BTO algorithm gradually slows down, and the LOCK algorithm also gradually decreases after the increases in acceleration value for a certain period. The proposed strategy optimizes the concurrency and improves the issue on transaction blocking. Therefore, the acceleration value has been maintained at a relatively stable level, which also slows down the performance decline caused by the increase in transaction traffic. With increasing CR, the acceleration values of several methods show a downward trend. However, in contrast, given the increase in CR, although the overall performance of the algorithm also shows a downward trend, the overall implementation of the proposed strategy is still slightly better than that of the other strategies.
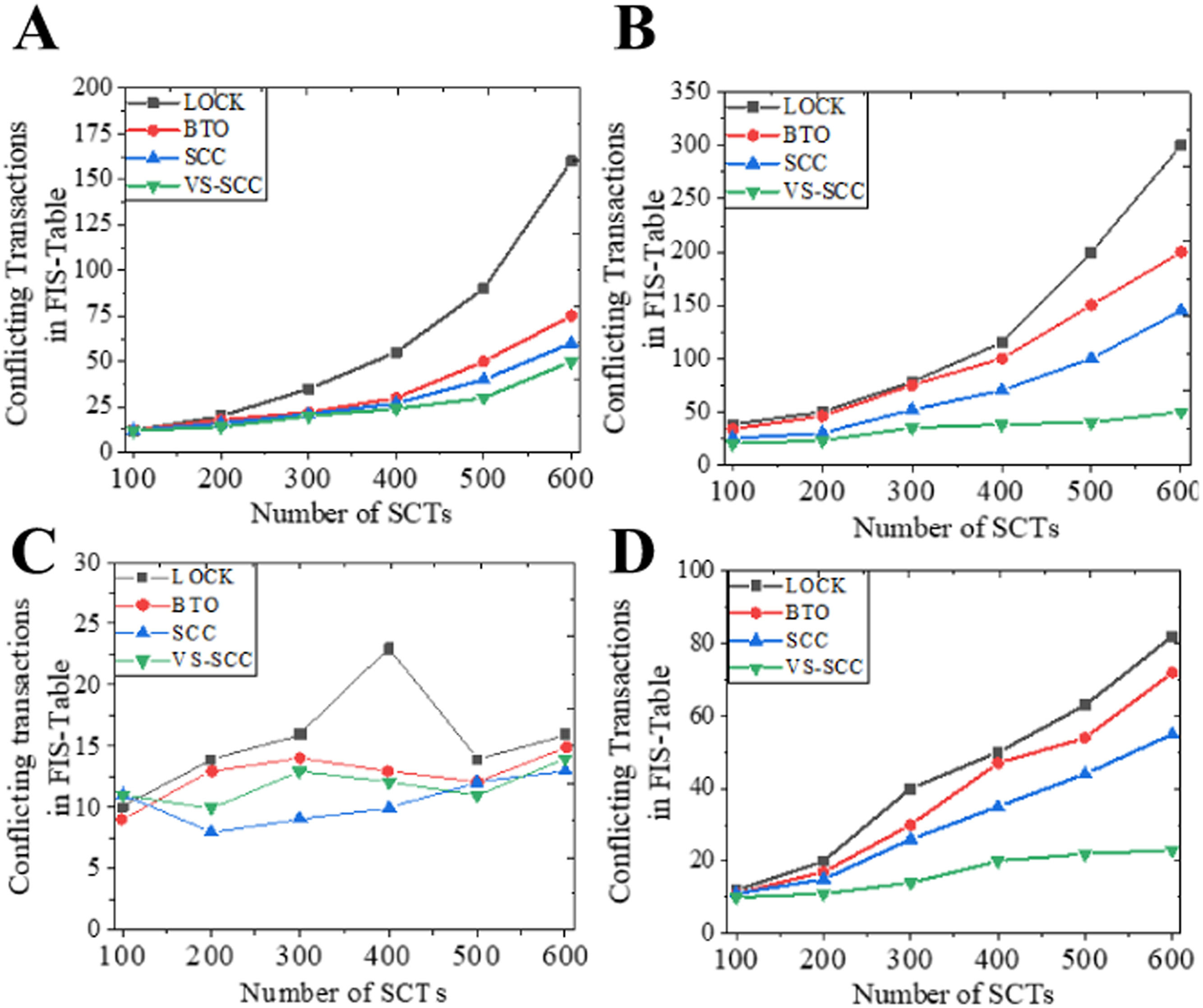
It compares the relationship between the number of superconduct tokens (SCT) corresponding to four types of SCs and conflict records under different concurrency control algorithms. The specific contents are shown in Fig. 7. For any method, conflict records will increase with a rise in the number of SCTs. However, in contrast, the VS-SCC algorithm optimizes the concurrency between SCTs. Thus, it has better performance. If the conflict records increase over time, more storage space will be consumed.
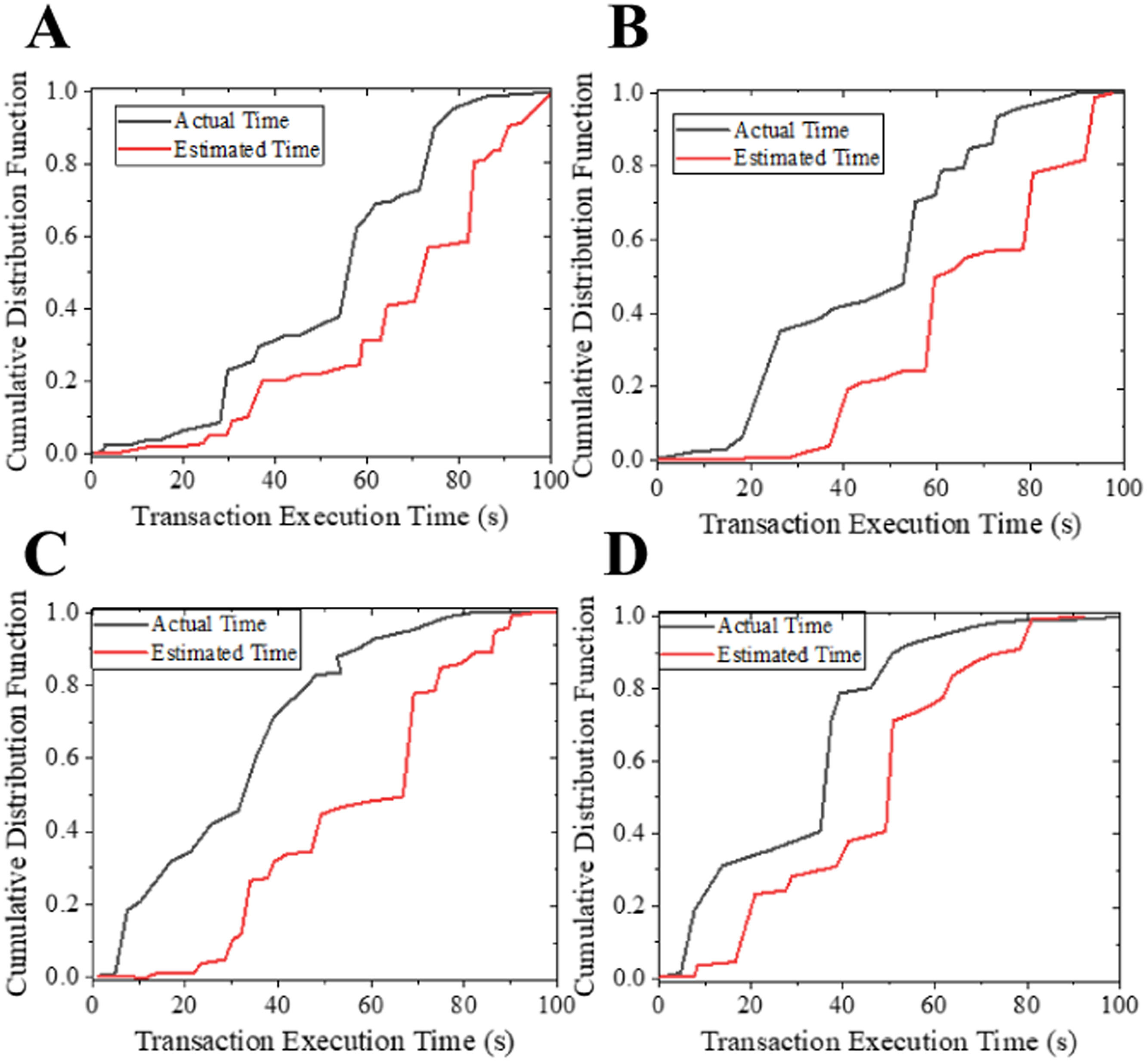
Next, it needs to predict the ET of SCs in the CAM-Unit. For the implementation of the four SCs, the real running time is slightly smaller than the estimated time. The ET is gradually reduced, and it overestimates the running time of the four SCs. The results show that the real-time distribution is relatively smooth and the estimated time is distributed in a ladder shape (Fig. 8). The estimated time obtained by the proposed algorithm is relatively rough. Moreover, good prediction results for SC transactions are easier to achieve with ladder-shaped real ET distributions.
Data traceability performance analysis of IP service systemThe data traceability performance analysis evaluates the performance of the proposed dynamic traceability algorithm. The number of attributes of the access policy is set to 4. Table 1 shows the comparison results of the encryption and decryption times of different schemes when the data sizes are 128 B, 256 B, 512 B, and 1,024 B. From the comparison curve of the encryption and decryption time of the improved CP-ABE scheme before and after the improvement, the identity parameter of the traceability manager is introduced into the improved CP-ABE scheme, which significantly increases the amount of computation of bilinear mapping. Consequently, the time costs of encryption and decryption are approximately 350 ms and 300 ms higher than that of the unimproved CP-ABE scheme, respectively. The algorithm sets the size of the encrypted and decrypted data to 128 B and the access attributes to 4, 8, 12, and 16 to obtain the corresponding encryption and decryption time. With the increase in the number of attributes, the encryption and decryption time consumption of the unimproved CP-ABE scheme is slightly better than that of this scheme. The ETs of encryption and decryption are saved by 500 ms and 300 ms, respectively.
Comparison of the encryption and decryption times of the CP-ABE scheme before and after improvement.
If the traceability manager wants to update the traceability information access policy, it can be realized by re-encryption or policy updates. The re-encryption process is divided into two steps: decrypting the original ciphertext and generating a new ciphertext. The policy update process is divided into two steps: new policy generation and new policy uplink. Fig. 9-A suggests the time cost of each step of the algorithm when the number of attributes of the encryption and decryption algorithm is set to 4, 8, 12, and 16. The total time consumption of re-encryption is approximately 150–650 ms higher than that of the policy update. This scheme not only meets the dynamic sharing of traceability information but also has some advantages in its access policy update algorithm. Fig. 9-B suggests the time consumption corresponding to the traceability operation process when the number of attributes is less than 16. The ET corresponding to the three steps of data uplink, traceability query, and policy update is within 2 s, and the time cost of each step also increases linearly with the increase in the number of attributes.
ConclusionThe IP system has become a strategic weapon for innovative countries to maintain technological advantages and realize groundbreaking development, thus demonstrating the essential attribute of institutional innovation. IP law originates from innovation and is the product of the innovation of the property rights system. With its continuous maturity, BD technology promotes the rapid development of information analysis and utilization and then brings broad application prospects for the layout of IP. The essence of institutional innovation and the goal of knowledge innovation of IP law are analyzed. Then, the value and obstacles of this innovation are discussed. In the industrial context involving a large number of IPs, the SC is optimized from the perspective of concurrency. Furthermore, the CTs are clustered, and a CAM-Unit is set up. The proposed policy optimizes the concurrency and improves the transaction blocking problem. Therefore, the acceleration value is maintained at a relatively stable level.
Blockchain technology is an important infrastructure to realize the digitalization of the economy. The full development and application of this technology can promote technological innovation and digital transformation. Smart contracts are an indispensable part of blockchain technology. In the traditional mode, IP right confirmation needs to undergo tedious procedures. However, by embedding a smart contract system, the IP rights of digital works can be automatically confirmed quickly. In the IP protection system, to realize the dynamic protection of transaction privacy, a policy-updatable attribute encryption algorithm is designed on the basis of the CP-ABE algorithm. Given that the identity parameters of the traceability manager are introduced into the improved CP-ABE scheme, the time costs of encryption and decryption are approximately 350 ms and 300 ms higher than those of the unimproved CP-ABE scheme, respectively. The technical model based on “blockchain + smart contract” proposed in this work realizes the design of an IP service system, which has important reference value for the institutional innovation of IP law. On the basis of the technology model of “blockchain + SC,” this work realizes the design of an IP service system. However, some limitations can still be improved. For complex scenes in actual situations, the designed system needs to be optimized further. Follow-up research will consider the consensus mechanism and design a consensus mechanism that can adapt to efficient service scenarios.
Supplementary material associated with this article can be found, in the online version, at doi:10.1016/j.compeleceng.2019.106522.
In the research of blockchain technology, IP service system and computer program system experiment in this Paper, we received guidance and assistance from Dr. Lv Zhihan. Thanks for Dr. Lv, for your careful guidance and unwavering support.